Microsoft SC-100 Study Guide: Microsoft Cybersecurity Architect Exam
- Sly Gittens

- Dec 17, 2022
- 4 min read
Updated: Dec 27, 2022
Tech Simplified Microsoft SC-100 Study Guide includes both free and paid resources to help you prepare and pass the Microsoft SC-100 Exam.

About Exam SC-100: Microsoft Certified: Cybersecurity Architect Expert
The Microsoft cybersecurity architect has subject matter expertise in designing and evolving the cybersecurity strategy to protect an organization's mission and business processes across all aspects of the enterprise architecture.
The cybersecurity architect designs a Zero Trust strategy and architecture, including security strategies for data, applications, access management, identity, and infrastructure. The cybersecurity architect also evaluates Governance Risk Compliance (GRC) technical strategies and security operations strategies.
SC-100 Microsoft Cybersecurity Architect Prerequisites
Before attending this course, students must have the following:
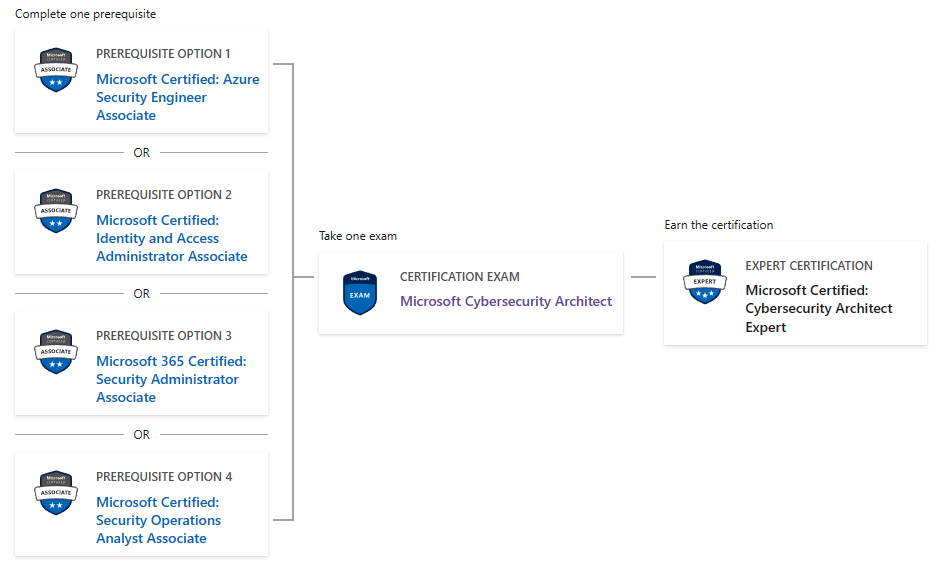
Highly recommended to have attended and passed one of the associate-level certifications in the security, compliance, and identity portfolio (such as AZ-500, SC-200, or SC-300)
Advanced experience and knowledge in identity and access, platform protection, security operations, securing data, and securing applications.
Experience with hybrid and cloud implementations.
Watch the SC-100 Study Guide Microsoft Cybersecurity Architect. 👇🏾
SC-100 Microsoft Learning Path
Don’t miss these free, self-paced online resources to help you gain the skills needed to earn your certification. SC-100 online learning path.
Tech Simplified University Training
Coming soon 1/16/23 (*May be sooner)
SC-100 Practice Exams
Microsoft Official Practice Tests are self-study tools that prepare candidates for the Microsoft required exams. $99.00 - $109.00 SC-100: Microsoft Cybersecurity Architect Microsoft Official Practice Test
Another practice test and sample questions. Free Examtopics.com Microsoft SC-100 Exam
Audience Profile for the Exam
This course is for experienced cloud security engineers who have taken a previous certification in the security, compliance, and identity portfolio. Specifically, students should have advanced experience and knowledge in various security engineering areas, including identity and access, platform protection, security operations, securing data, and securing applications. They should also have experience with hybrid and cloud implementations. Beginning students should instead take the course SC-900: Microsoft Security, Compliance, and Identity Fundamentals.
About Exam SC-100: Microsoft Cybersecurity Architect
This is an advanced, expert-level course. Although not required to attend, students are strongly encouraged to have taken and passed another associate-level certification in the security, compliance, and identity portfolio (such as AZ-500, SC-200, or SC-300) before attending this class. This course prepares students with the expertise to design and evaluate cybersecurity strategies in the following areas: Zero Trust, Governance Risk Compliance (GRC), security operations (SecOps), and data and applications. Students will also learn how to design and architect solutions using zero trust principles and specify security requirements for cloud infrastructure in different service models (SaaS, PaaS, IaaS).
Skills Measured
For the full list of the skills that the exam measures, along with the level of experience and expertise that you’ll need as an exam candidate, check out the skills measured.
Design a Zero Trust strategy and architecture (30-35%)
Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies (10-15%)
Design security for infrastructure (10-15%)
Design a strategy for data and applications (15-20%)
Recommend security best practices and priorities (20-25%)
SC-100 Articles / Blog Posts Per Objective
Design a Zero Trust strategy and architecture (30–35%)
Build an overall security strategy and architecture
Design a security operations strategy
Design a logging and auditing strategy to support security operations
Develop security operations to support a hybrid or multi-cloud environment
Evaluate a security operations strategy for the incident management lifecycle
Evaluate a security operations strategy for sharing technical threat intelligence
.png)



Comments